Okta SAML
Learn how to set up SAML-based Single Sign-On (SSO) using Okta as your Identity Provider, with step-by-step instructions for enterprise application configuration.
This guide walks you through configuring Okta as your SAML identity provider for the application you are onboarding, enabling secure single sign-on for your users. You’ll learn how to set up an enterprise application, configure SAML settings to the host application. By following these steps, your users will be able to seamlessly authenticate using their Okta credentials.
Create Enterprise Application
Section titled “Create Enterprise Application”-
Login to your Okta Admin Console. Go to Applications→ Applications.
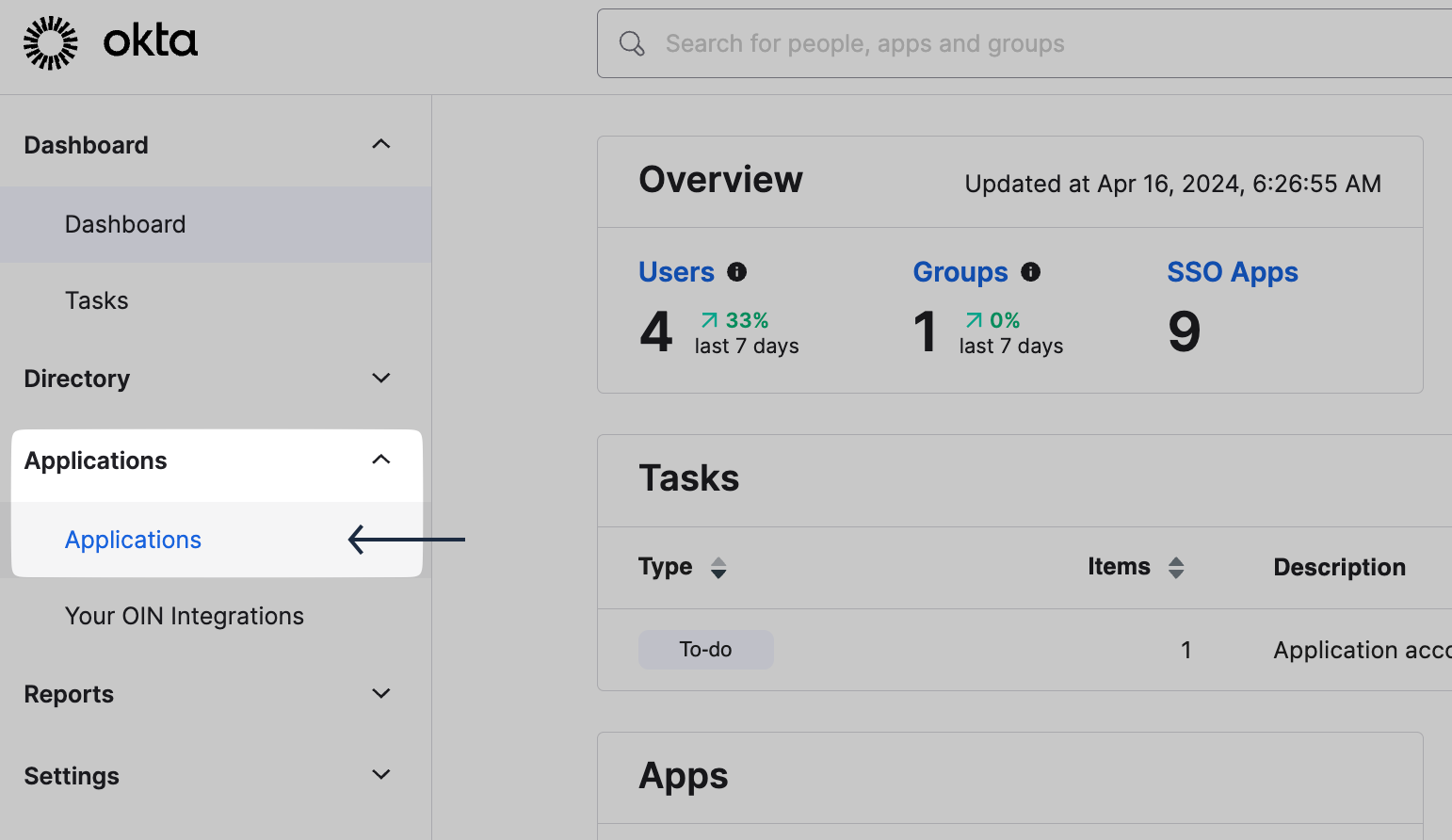
-
In the Applications tab, click on Create App Integration.
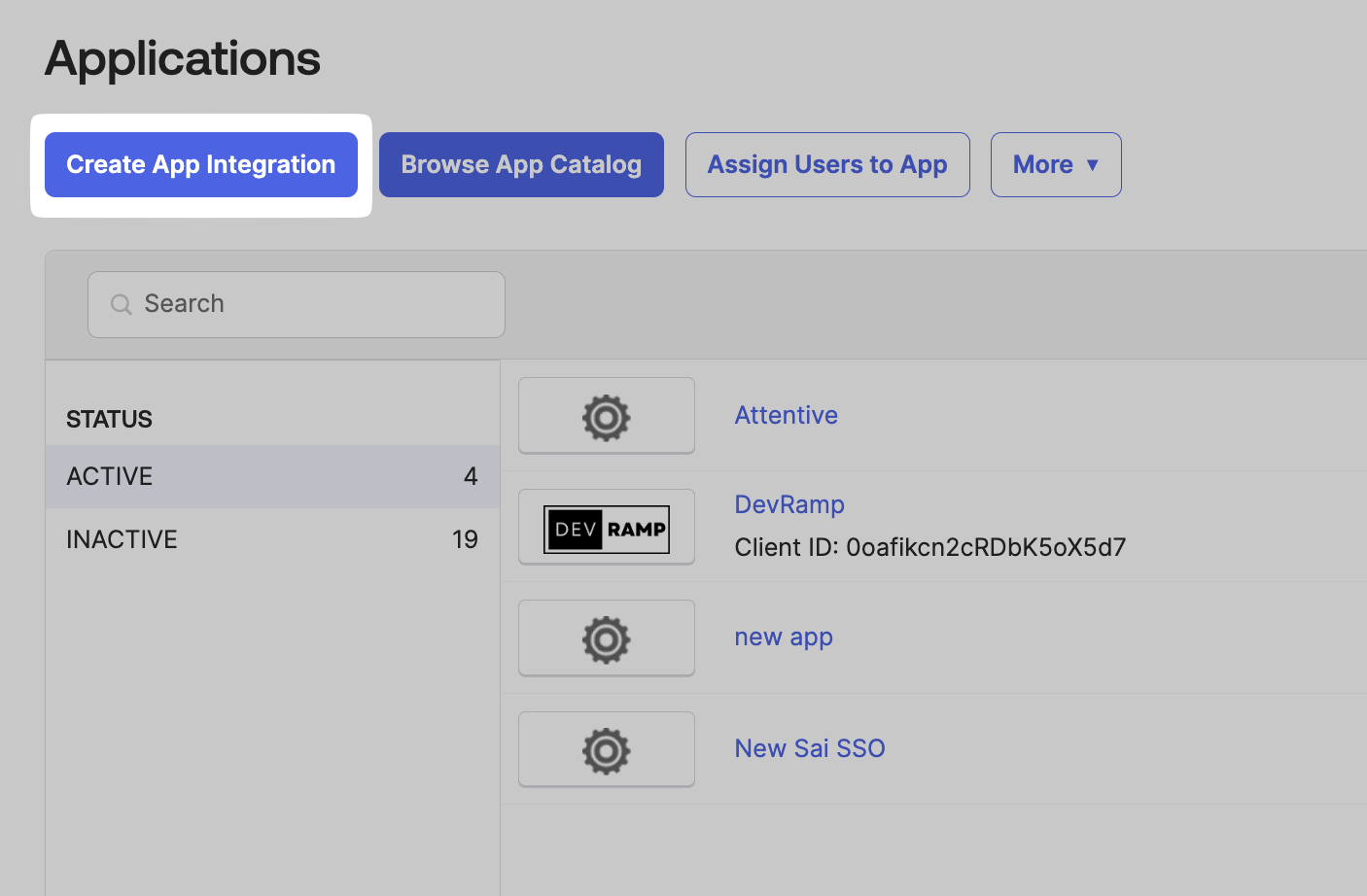
-
Choose SAML 2.0, and click on Next.
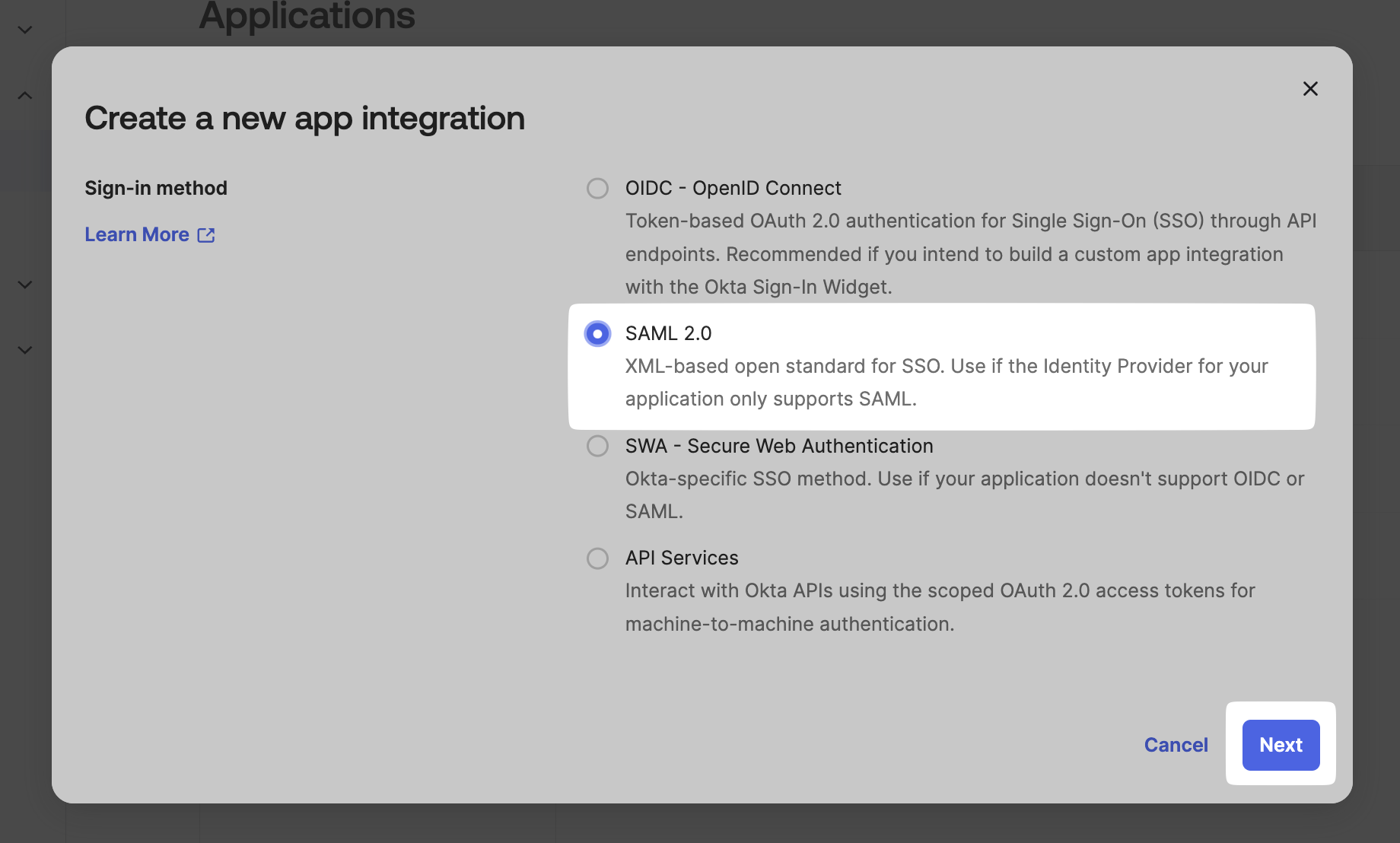
-
Give your app a name, choose your app visibility settings, and click on Next.
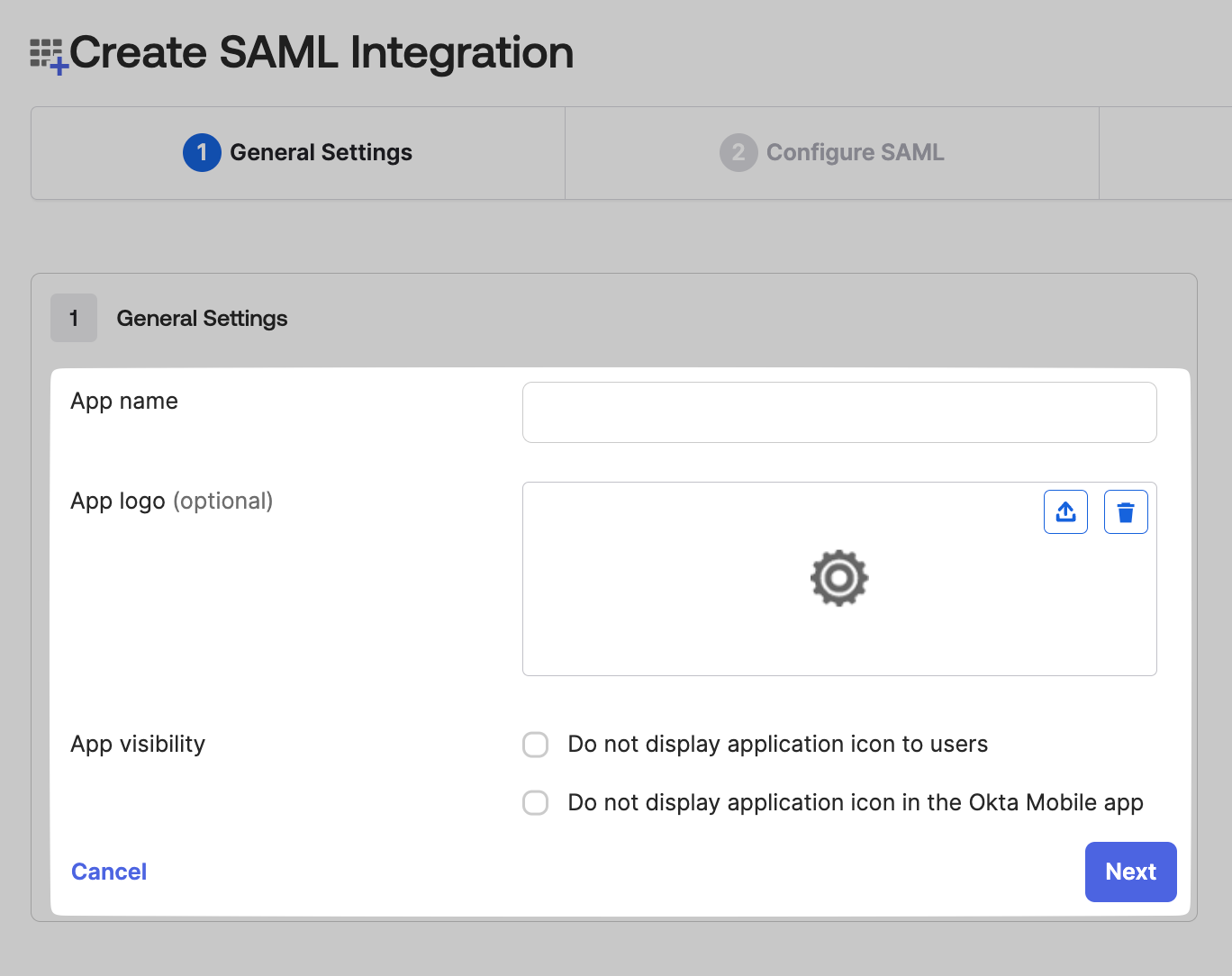
SAML Configuration
Section titled “SAML Configuration”-
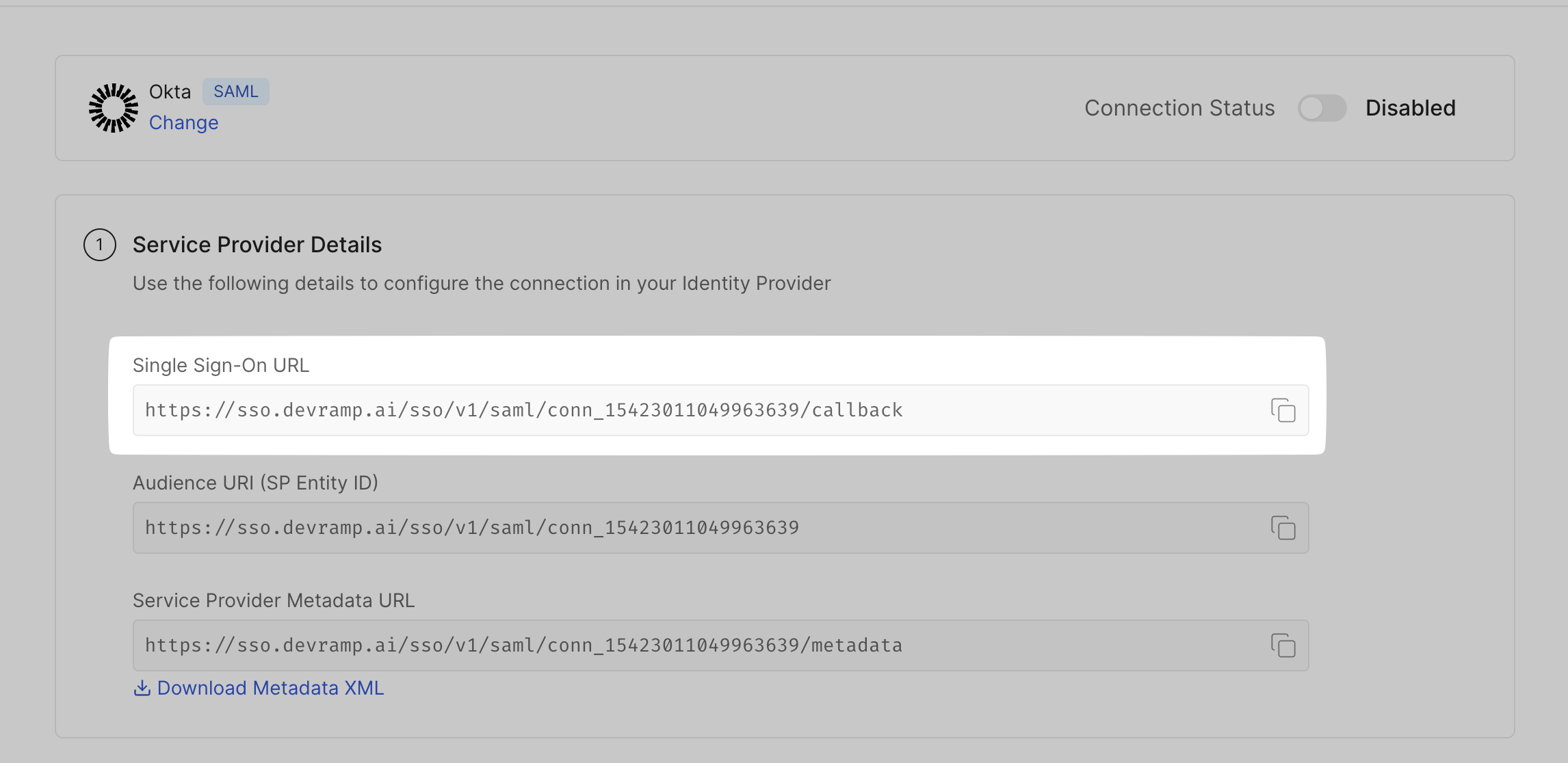
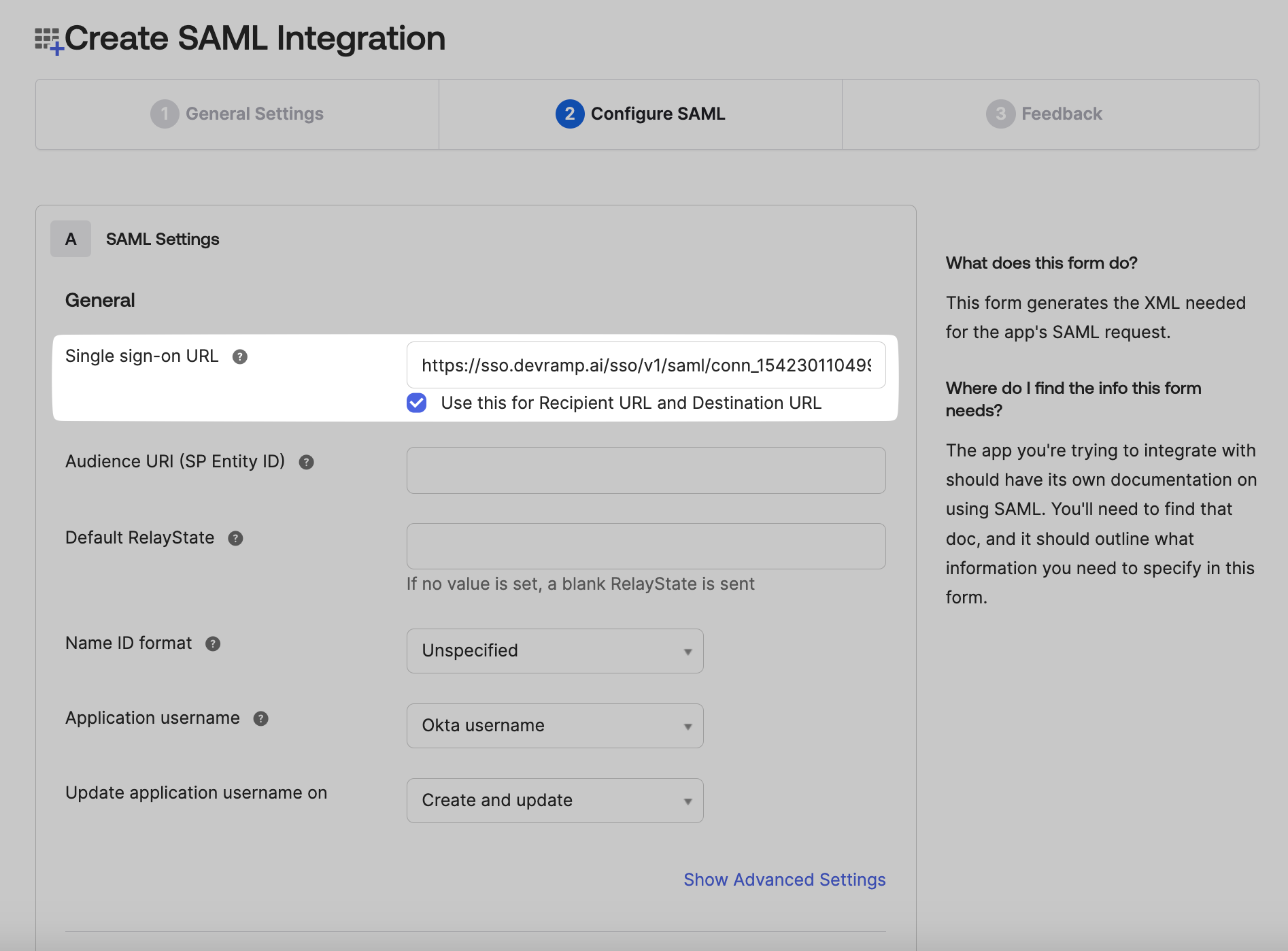
Copy the SSO URL from the SSO Configuration Portal. Paste this link in the space for SSO URL on the Okta Admin Console.
-
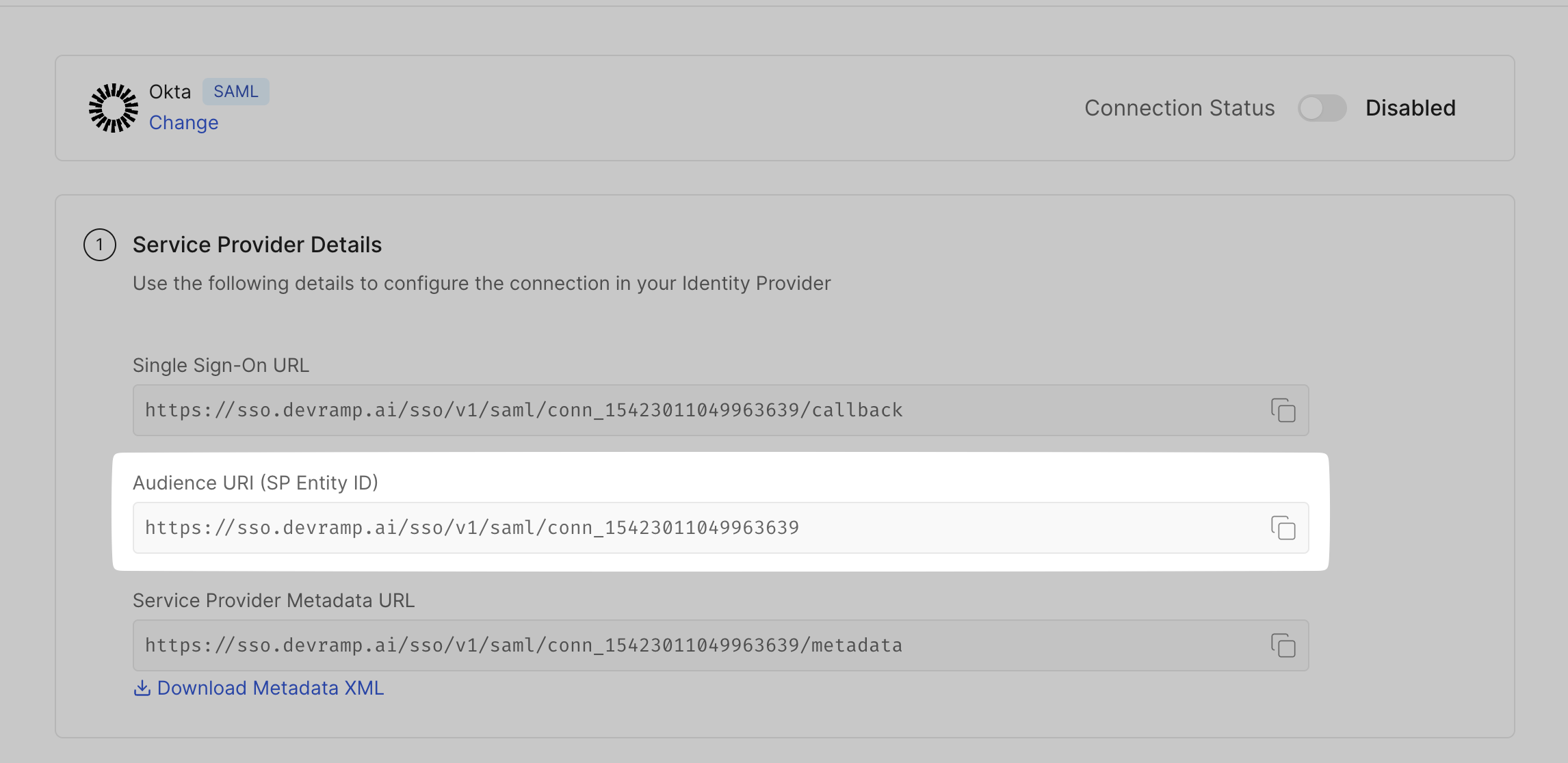
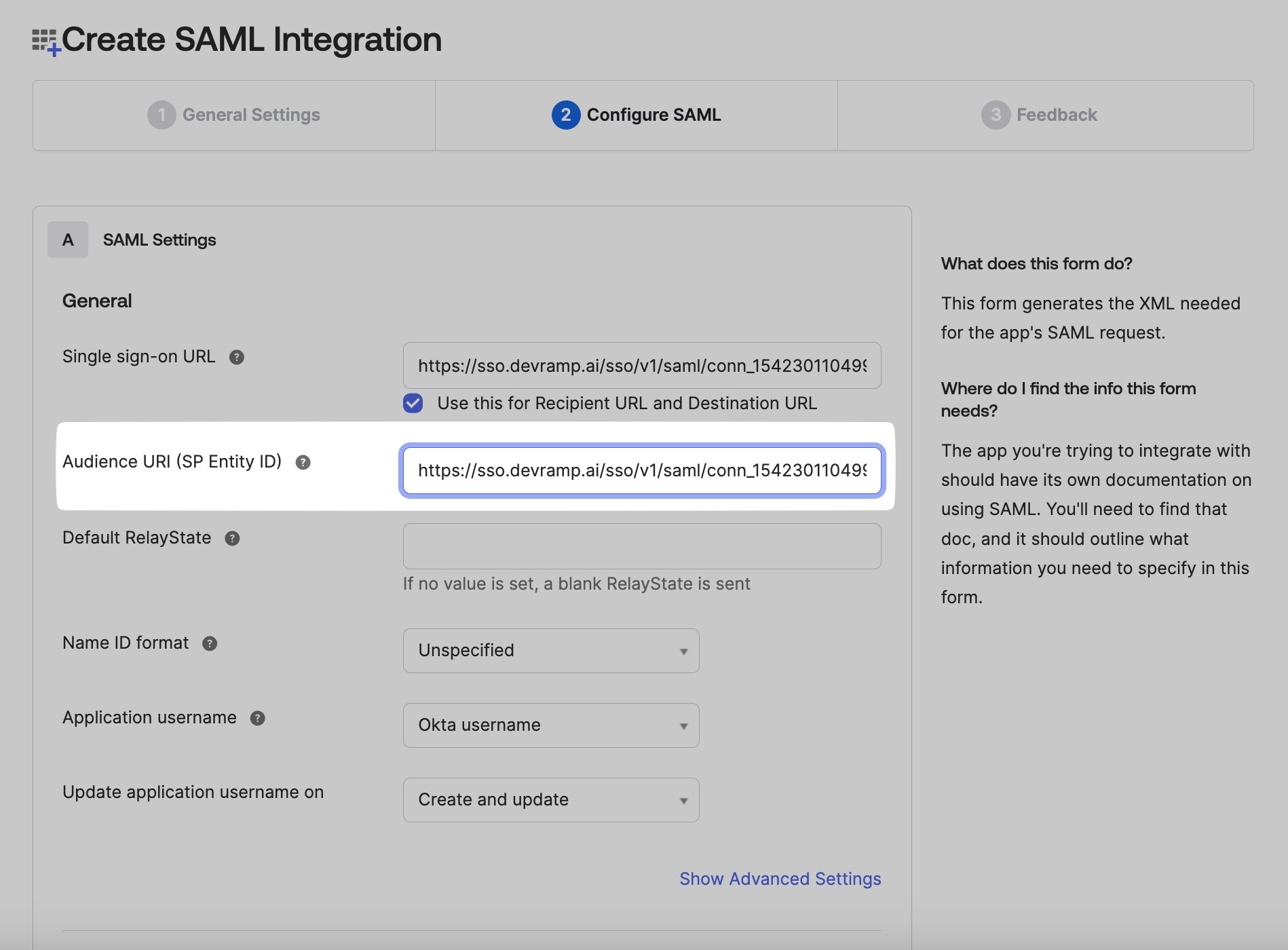
Copy the Audience URI (SP Entity ID) from the SSO Configuration Portal, and paste it in your Okta Admin Console in the space for Audience URI.
-
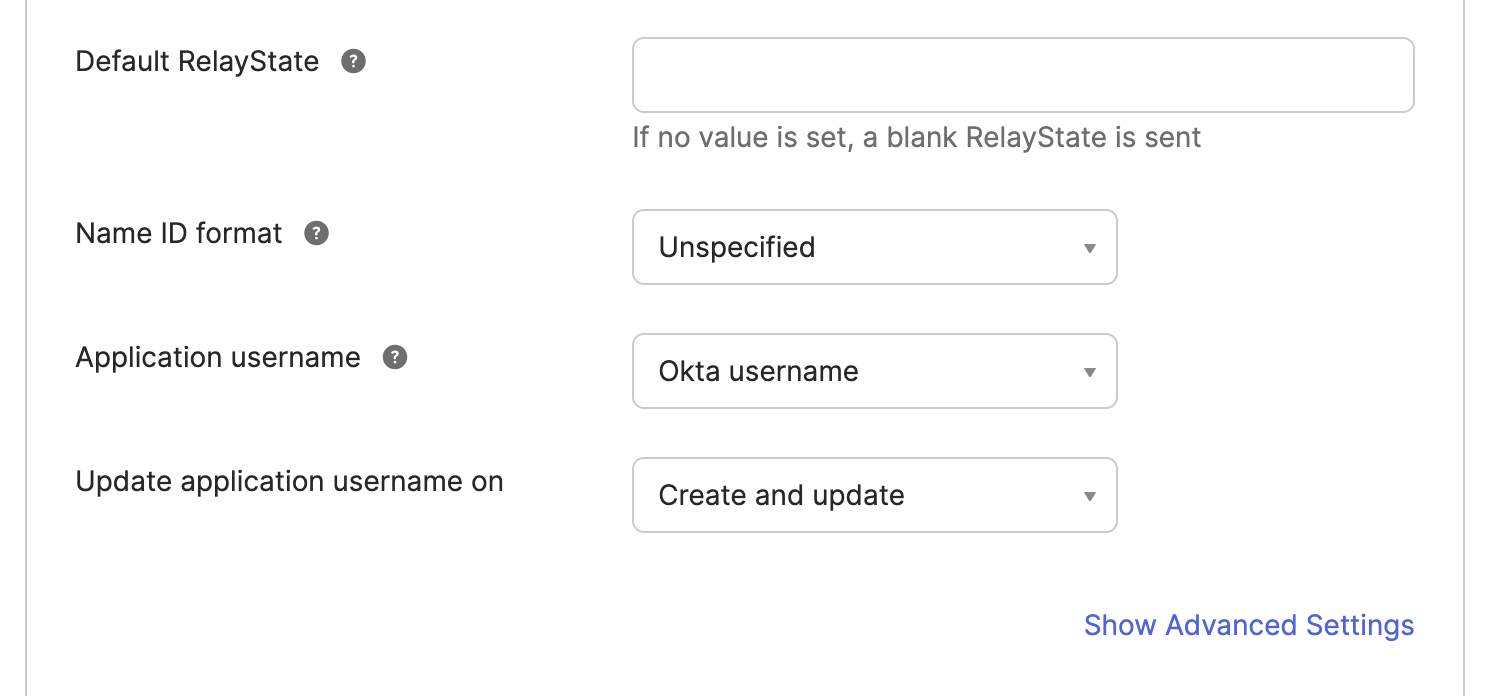
You can leave the Default Relay State as blank. Similarly, select your preferences for the Name ID format, Application Username, and Update application username on fields.
Attribute Mapping
Section titled “Attribute Mapping”-
Check the Attribute Statements section in the SSO Configuration Portal, and carefully map the same attributes on your Okta Admin Console. There are 2 ways that you may perform the mapping here. You may either use the Add expression buttons to add your attributes or through the legacy configurations. You will need to click on Add expression to add your required attributes.
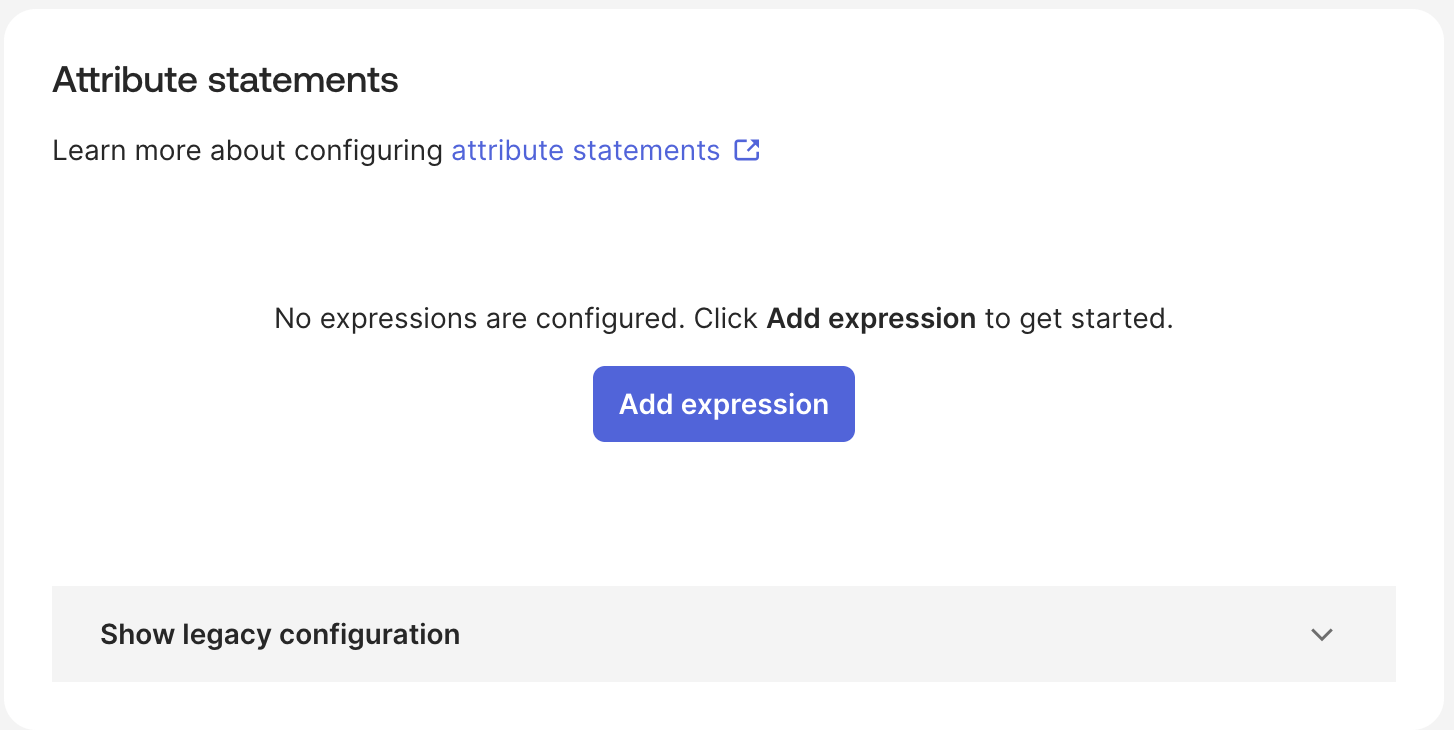
-
You will have to enter each attribute one by one as shown below. click on Save once you have added the name and value for the attribute,
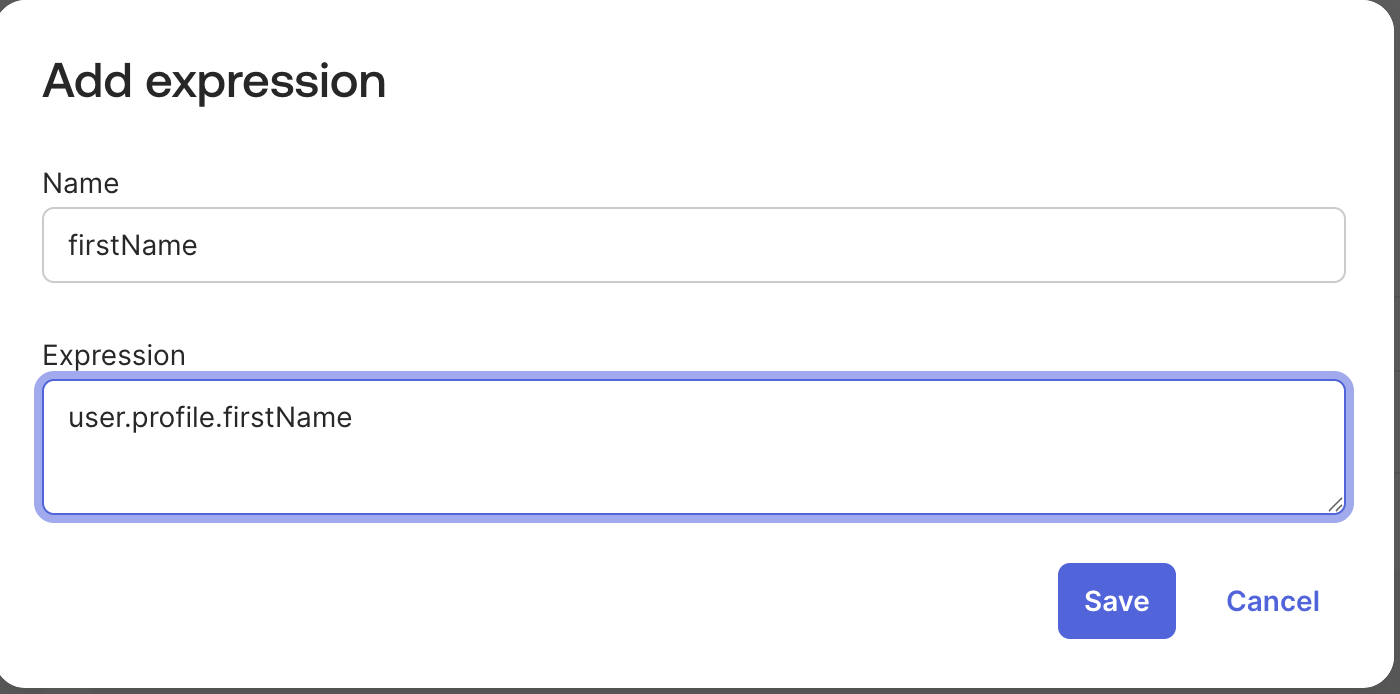
-
Ensure that you map all the required attributes as shown on the SSO Configuration Portal.
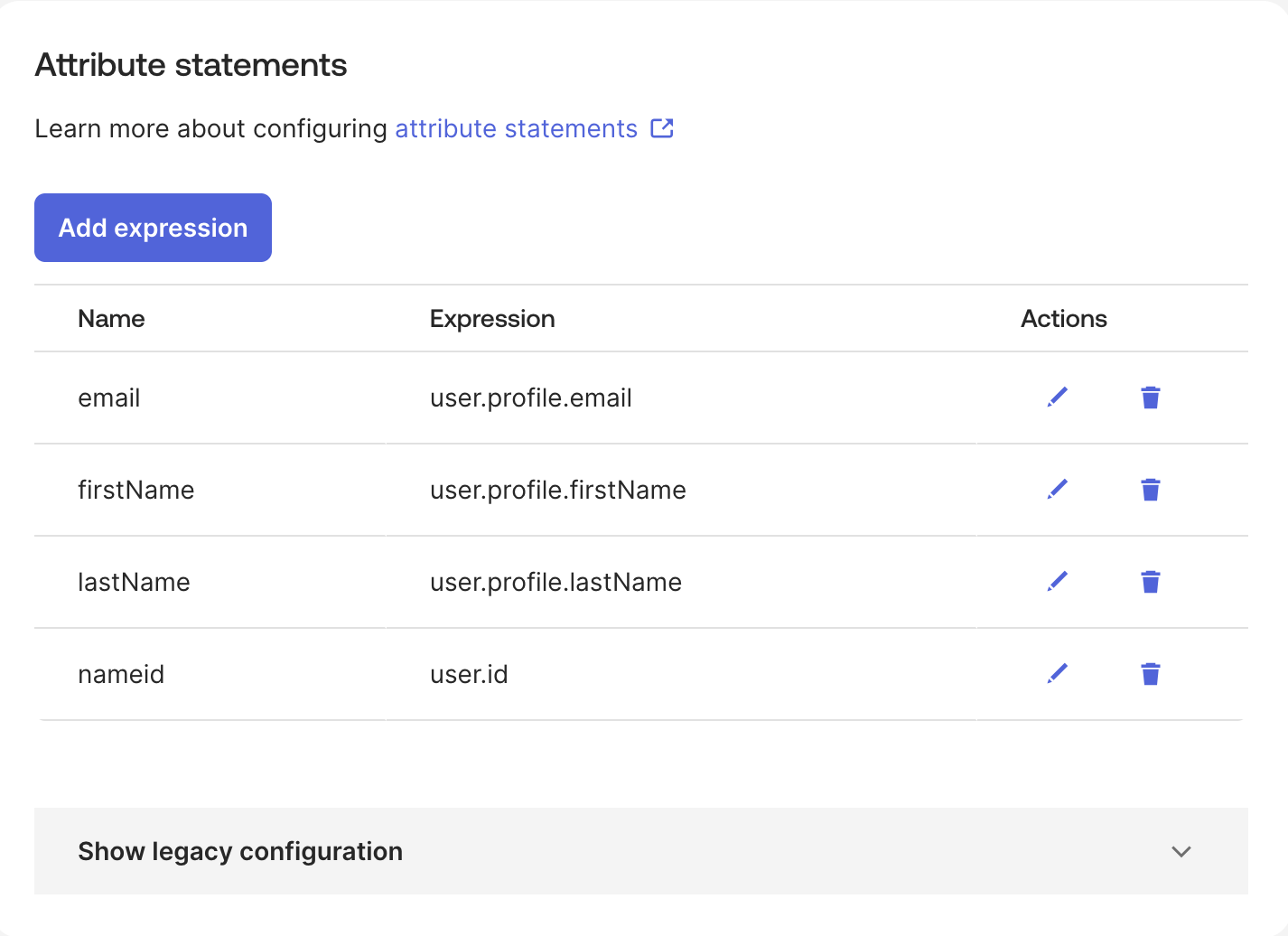
Assign User/Group
Section titled “Assign User/Group”-
Go to the Assignments tab.
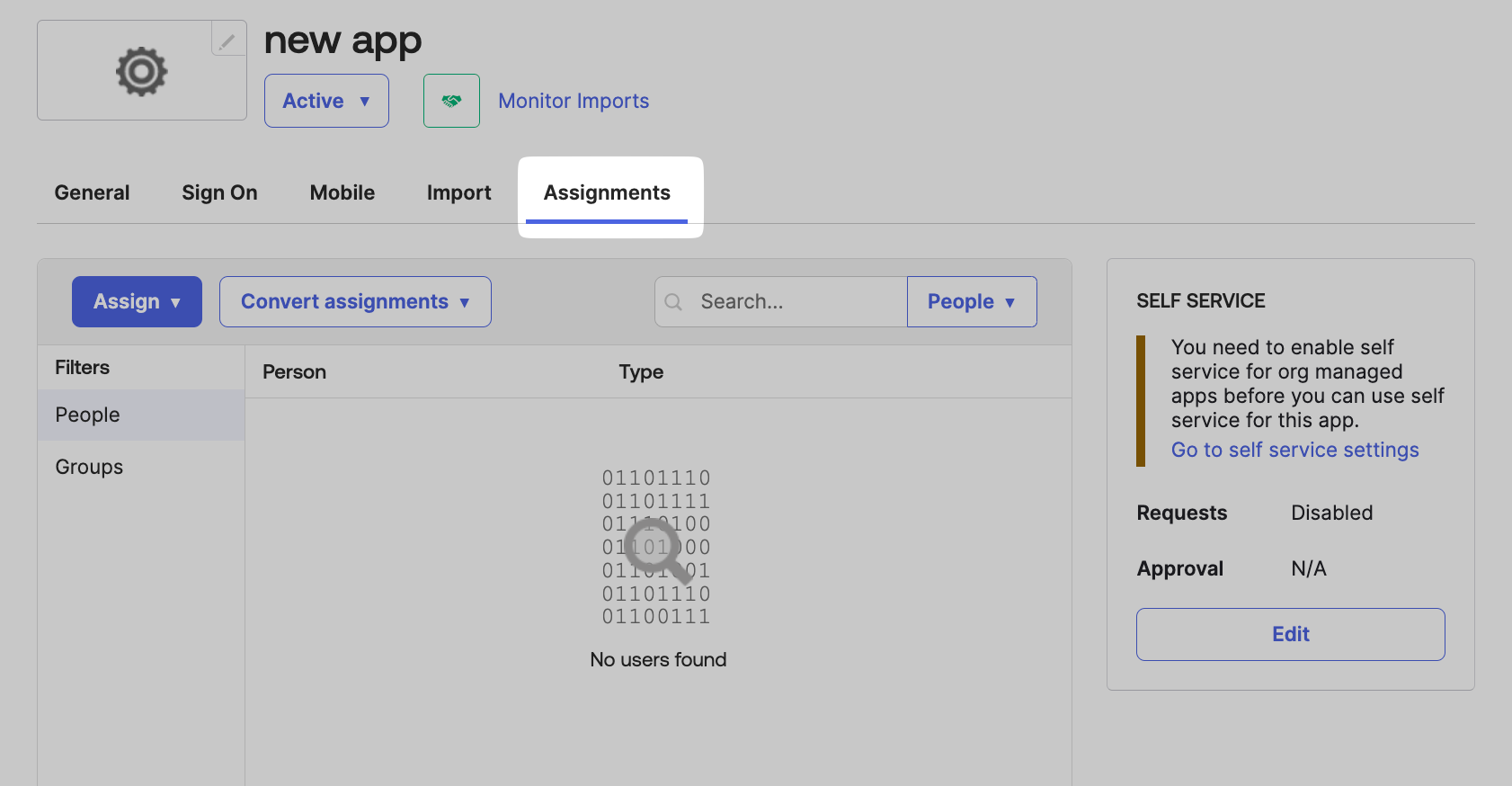
-
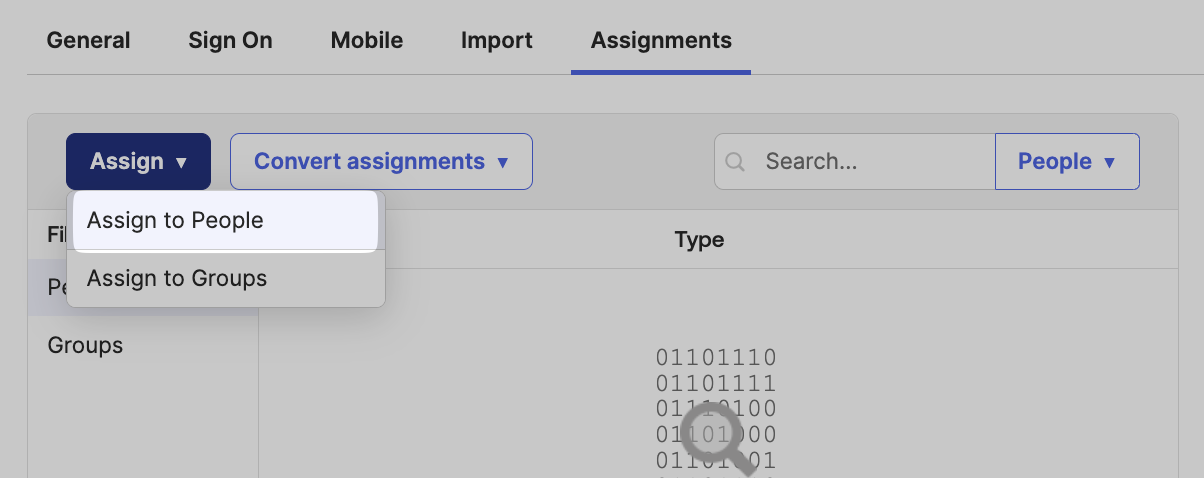
Click on Assign on the top navigation bar, select Assign to People/Groups.
-
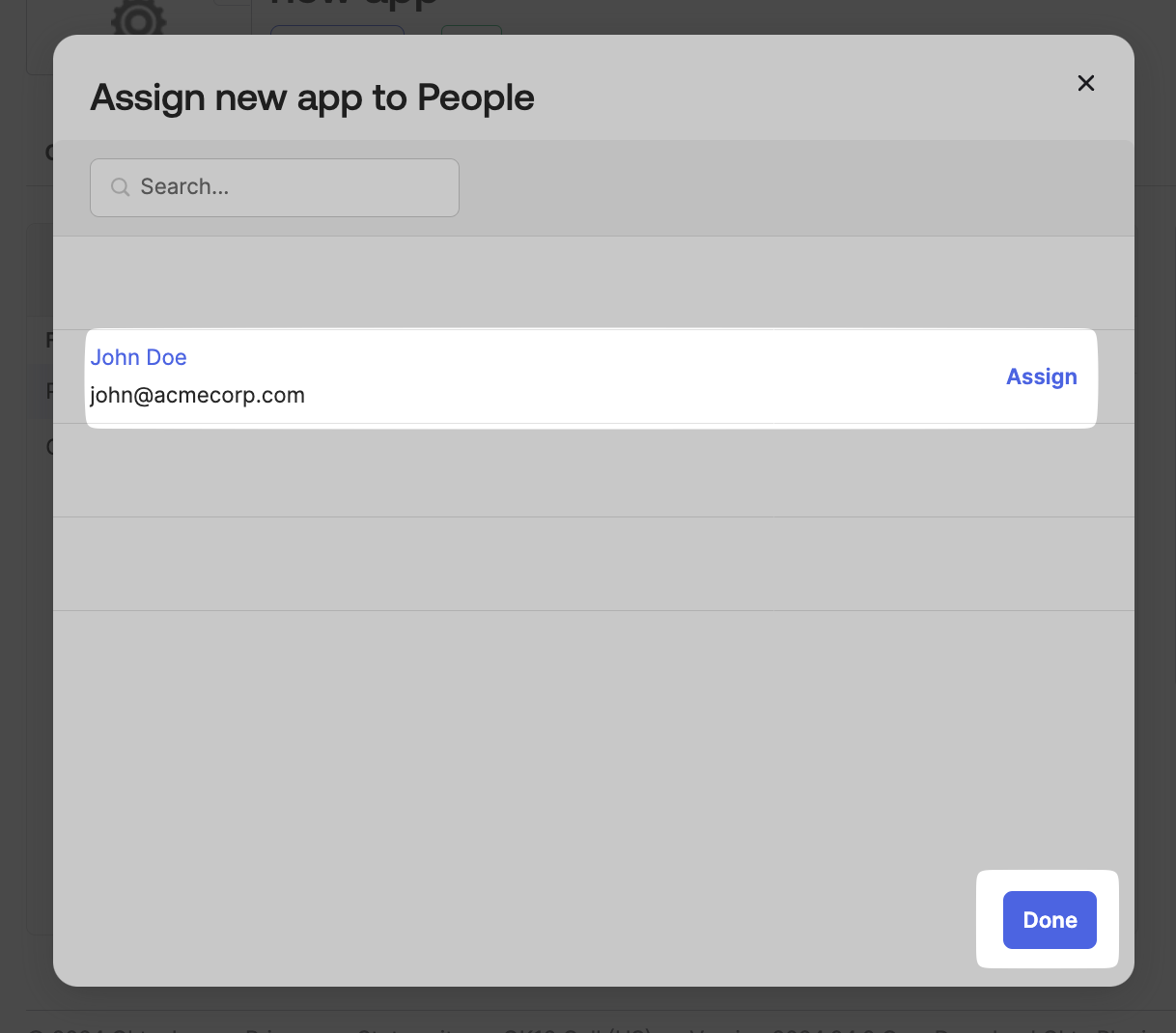
Click on Assign next to the people you want to assign it to. Click on Save and Go Back, and click on Done.
Finalize App
Section titled “Finalize App”-
Preview your SAML Assertion generated, and click on Next.
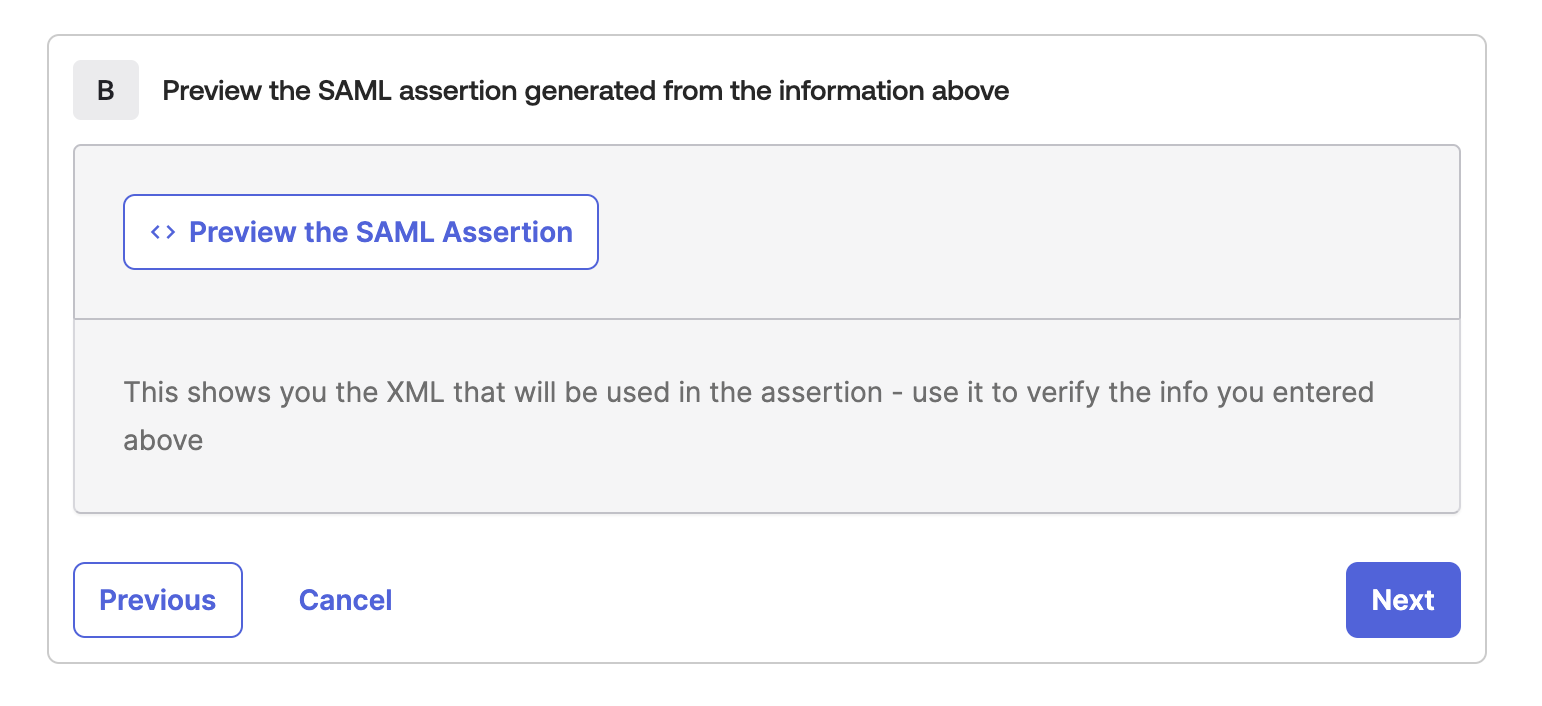
-
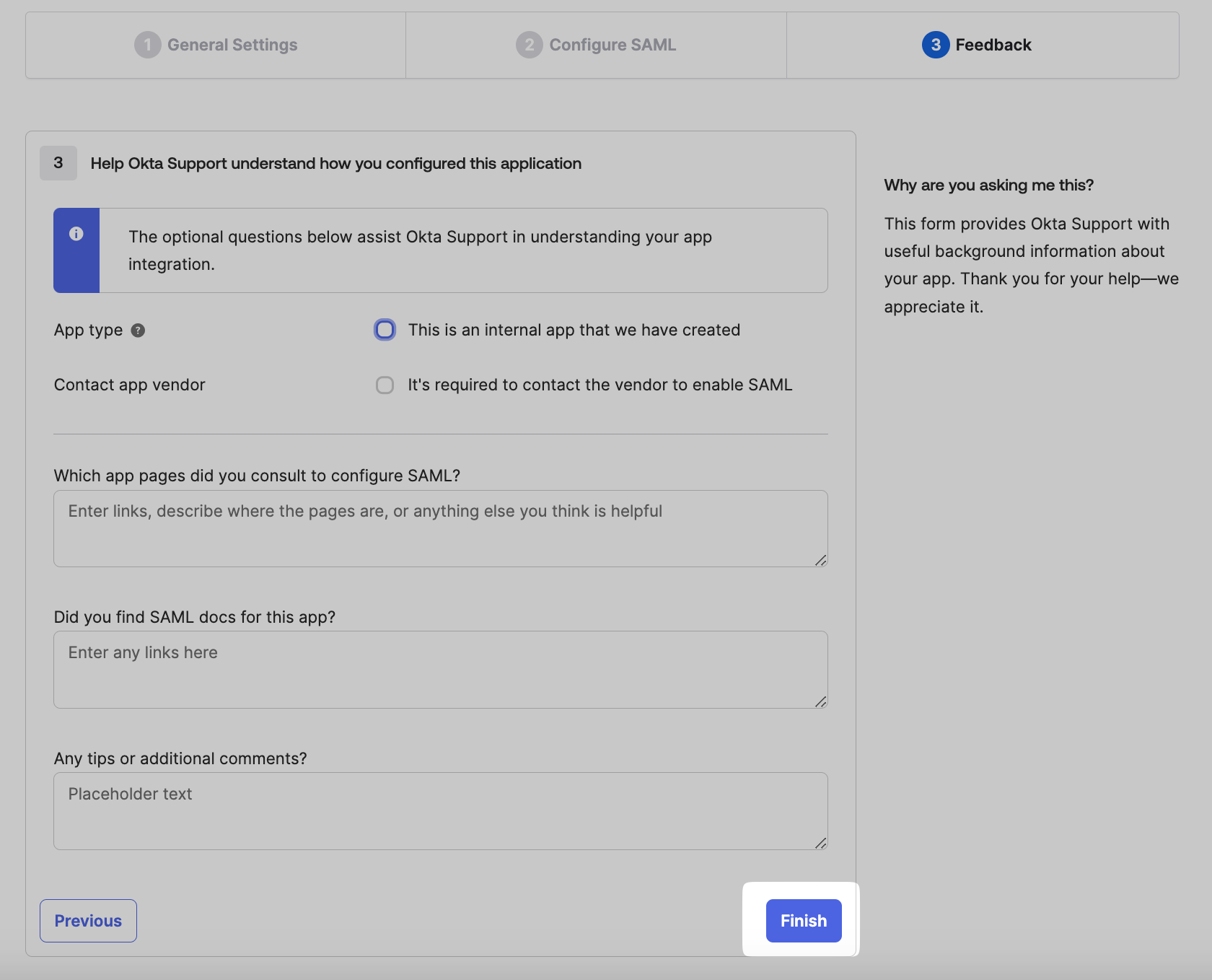
Fill the feedback form, and click on Finish once done.
Upload IdP Metadata URL
Section titled “Upload IdP Metadata URL”-
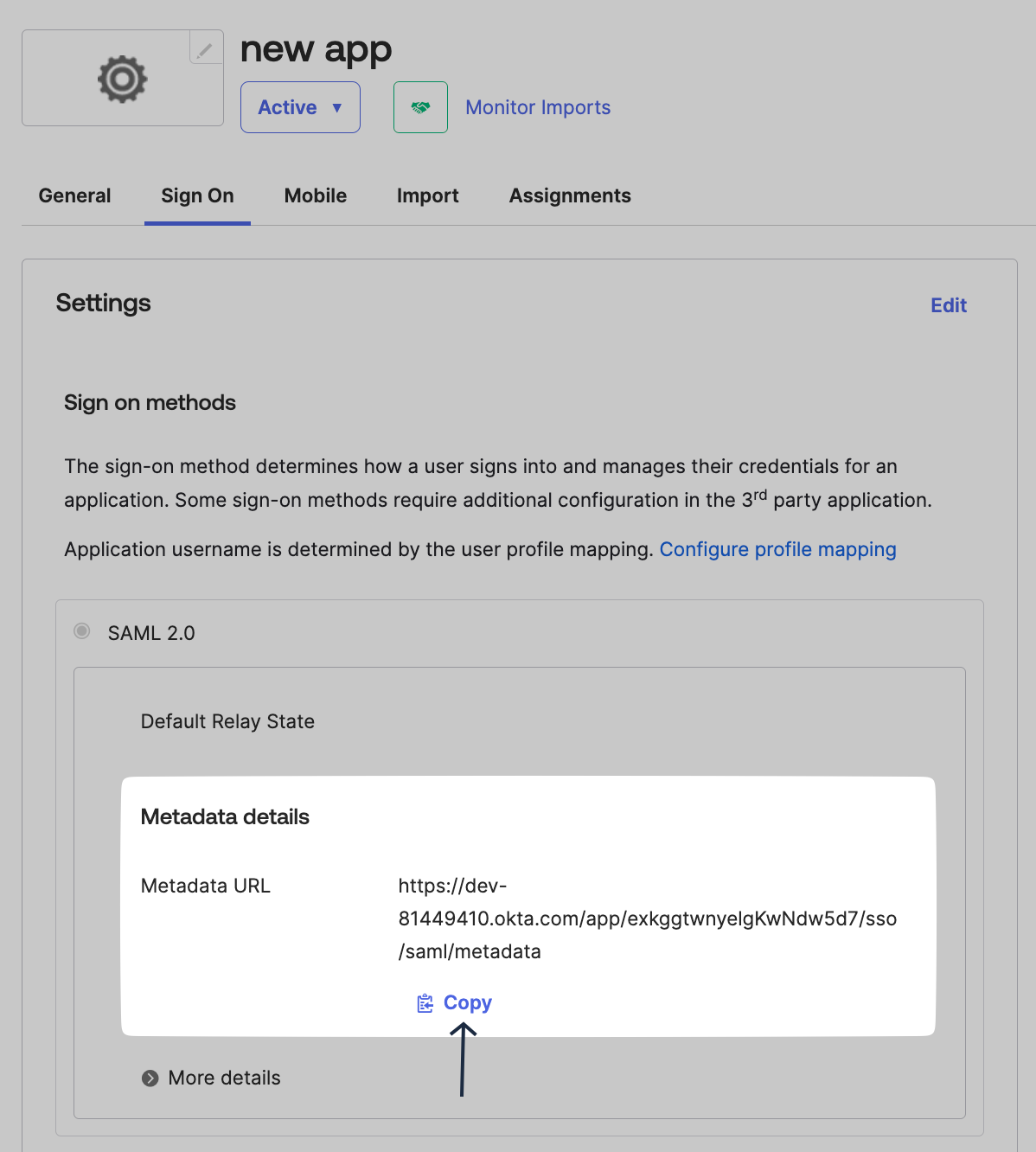
On the Sign On tab copy the Metadata URL from the Metadata Details section on Okta Admin Console.
-
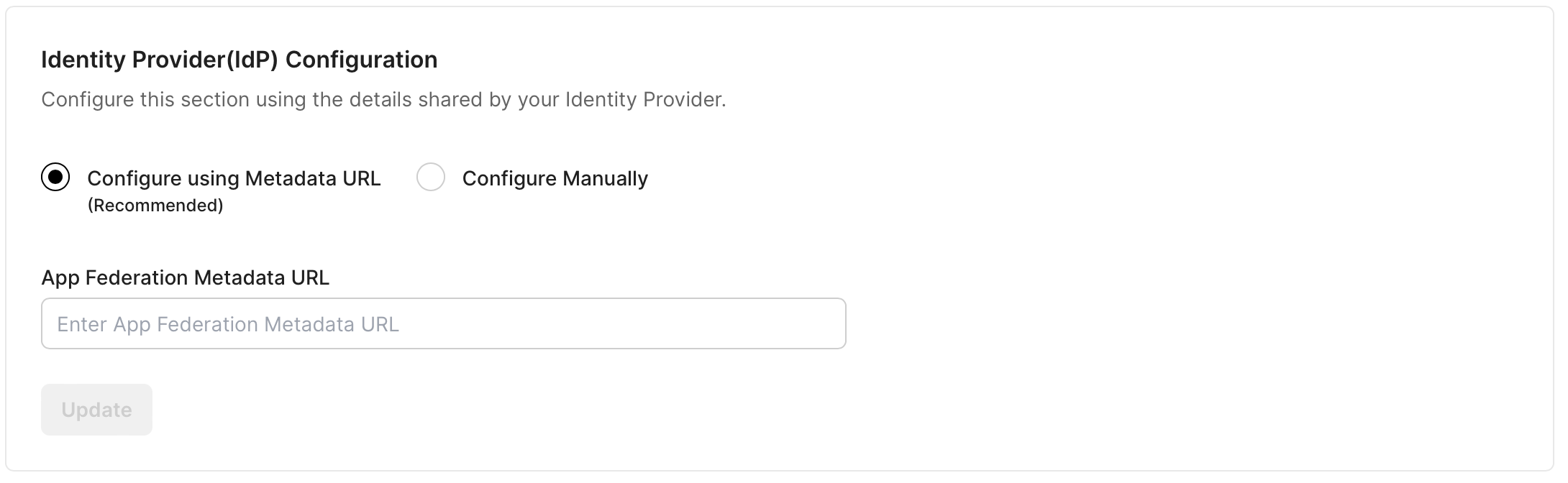
Under Identify Provider Configuration, select Configure using Metadata URL, and paste it under App Federation Metadata URL on the SSO Configuration Portal.
Test Connection
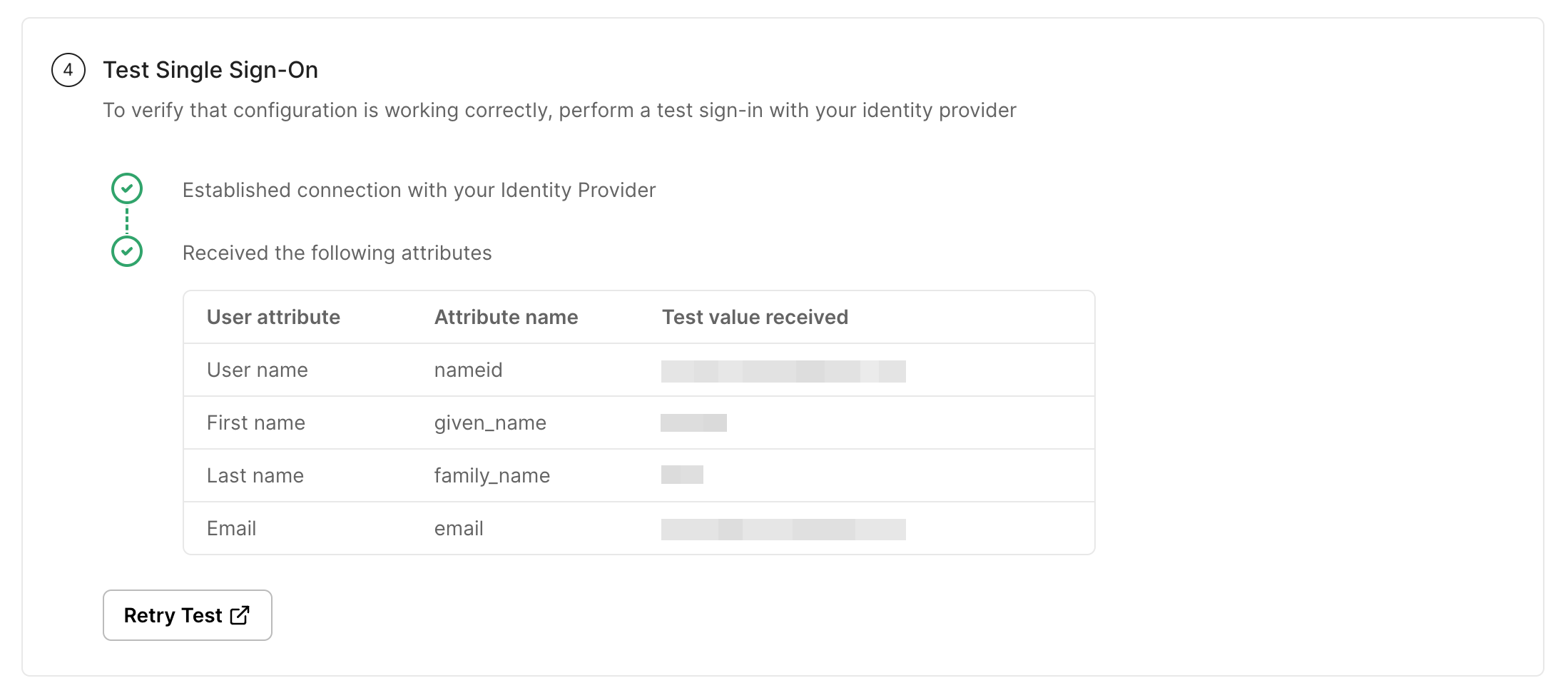
Section titled “Test Connection”Click on Test Connection. If everything is done correctly, you will see a Success response as shown below.
Enable Connection
Section titled “Enable Connection”Click on Enable Connection. This will let all your selected users login to the new application via your Okta SSO.
With this, we are done configuring your Okta application for an SSO login setup.