Secure MCP with Enterprise SSO
Use Scalekit's out-of-the-box enterprise SSO connections to authenticate your MCP server from the first request.
Scalekit automatically handles identity verification via any authentication method, including but not limited to social providers like Google and Microsoft. It also supports authentication with your enterprise identity provider, such as Okta, Microsoft Entra AD, or ADFS, via SAML or OIDC.
In this article, we will explain how to configure an Enterprise SSO connection with Okta as an identity provider. You can follow the same steps to configure any other identity provider. The steps with blue arrows indicate that the step occurs during the browser redirects and the steps with the red arrows are Headless or Machine-to-Machine operations happening in the background.
Understanding the MCP SSO Flow at a high level
Section titled “Understanding the MCP SSO Flow at a high level”Before you start
Section titled “Before you start”Please make sure you have implemented MCP Auth with any of these examples.
Configure Okta for authentication
Section titled “Configure Okta for authentication”-
To configure Enterprise SSO, you need to create an organization.
Open the Scalekit Dashboard -> Organizations -> Create Organization.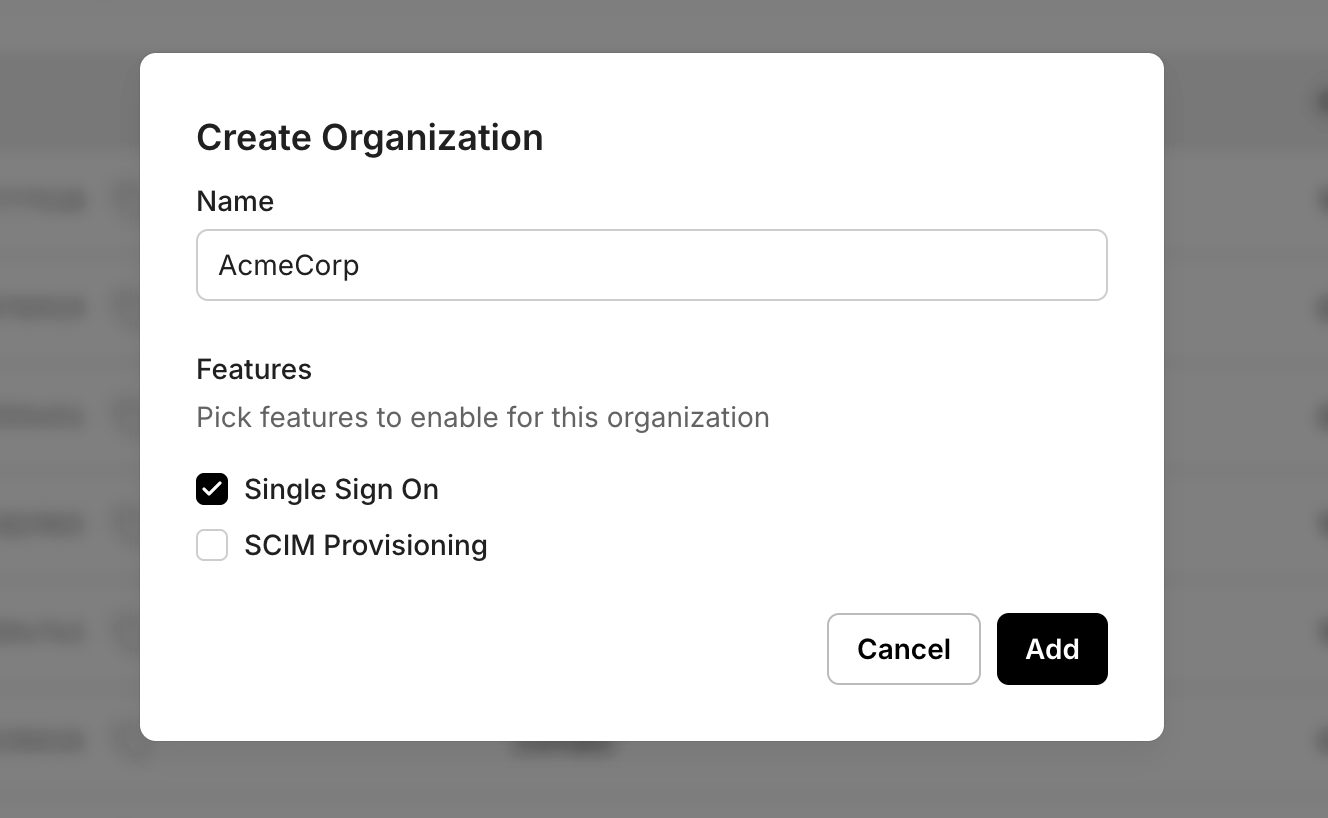
-
Navigate to the Single Sign-On tab and follow the on-screen instructions. Make sure to click Test Connection, and then Enable Connection.
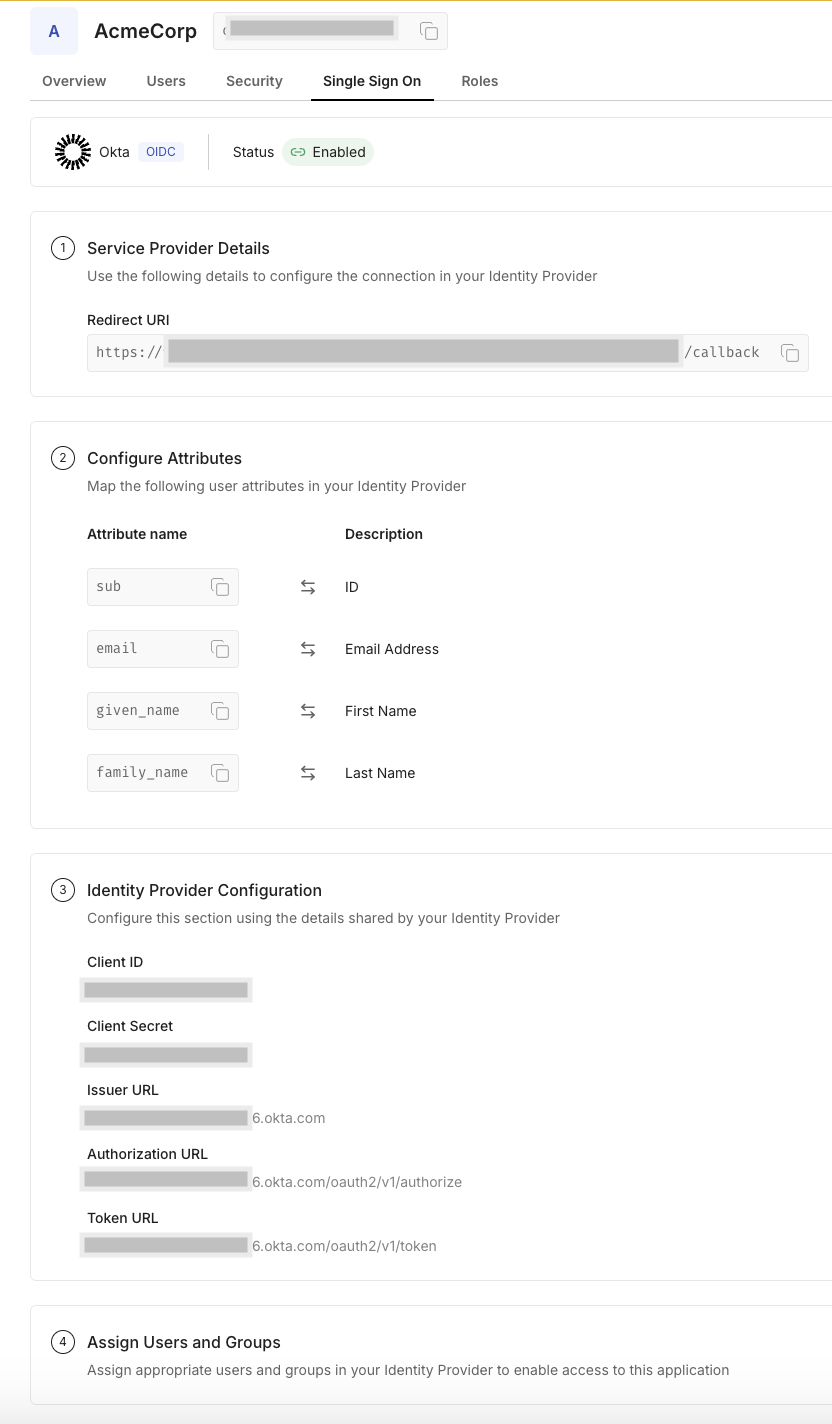
-
To enforce that users from this organization are authenticated with the identity provider, add the domain under the Domains section in the Overview tab (e.g.,
acmecorp.com).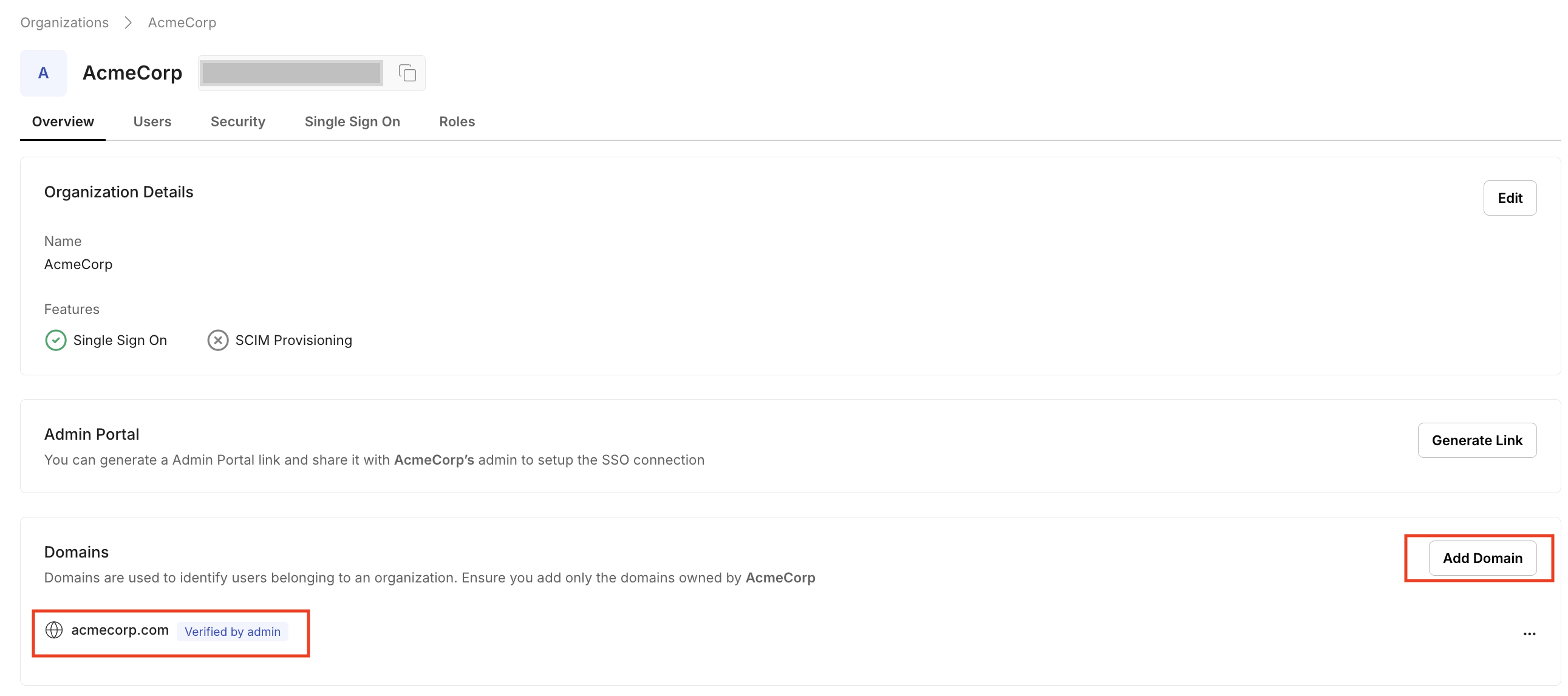
You have successfully implemented Enterprise SSO for your MCP server. Try running any of the example apps next.
If you don’t have access to the Identity Provider console
You can generate an Admin Portal link from Scalekit and share it with your IT admin.