Agent / Machine interacting with MCP Server
Learn how an autonomous agent or machine securely authenticates with an MCP Server using OAuth 2.1 Client Credentials flow in Scalekit.
An autonomous agent or any machine-to-machine process can directly interact with an MCP Server secured by Scalekit. In this model, the agent acts as a confidential OAuth client, authenticated using a client_id and client_secret issued by Scalekit.
This topology uses the OAuth 2.1 Client Credentials flow, allowing the agent to obtain an access token without user interaction. Tokens are scoped and time-bound, ensuring secure and auditable automation between services.
Authorization Sequence
Section titled “Authorization Sequence”How It Works
Section titled “How It Works”Client Registration Before an agent can request tokens, you must create a Machine-to-Machine (M2M) client for your MCP Server in Scalekit.
Steps to create a client:
- Navigate to Dashboard ? MCP Servers and select your MCP Server. Go to the Clients tab.
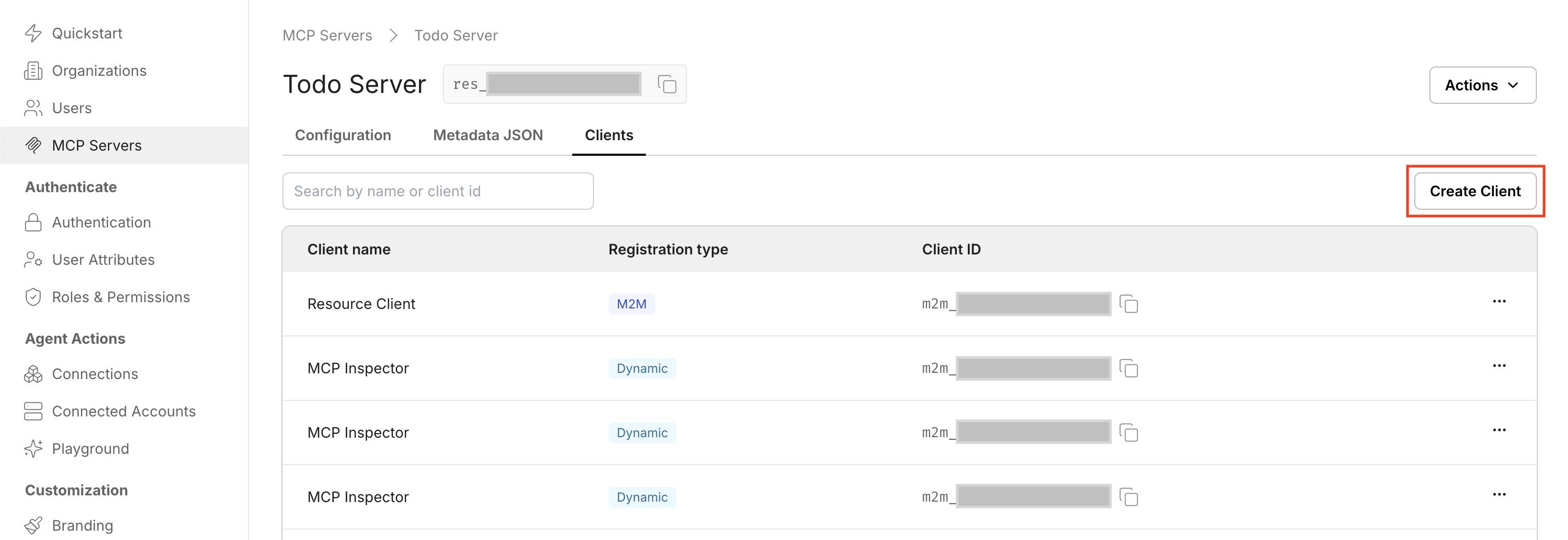
- Click Create Client.
- Copy the client_id and client_secret immediately - the secret will not be shown again.
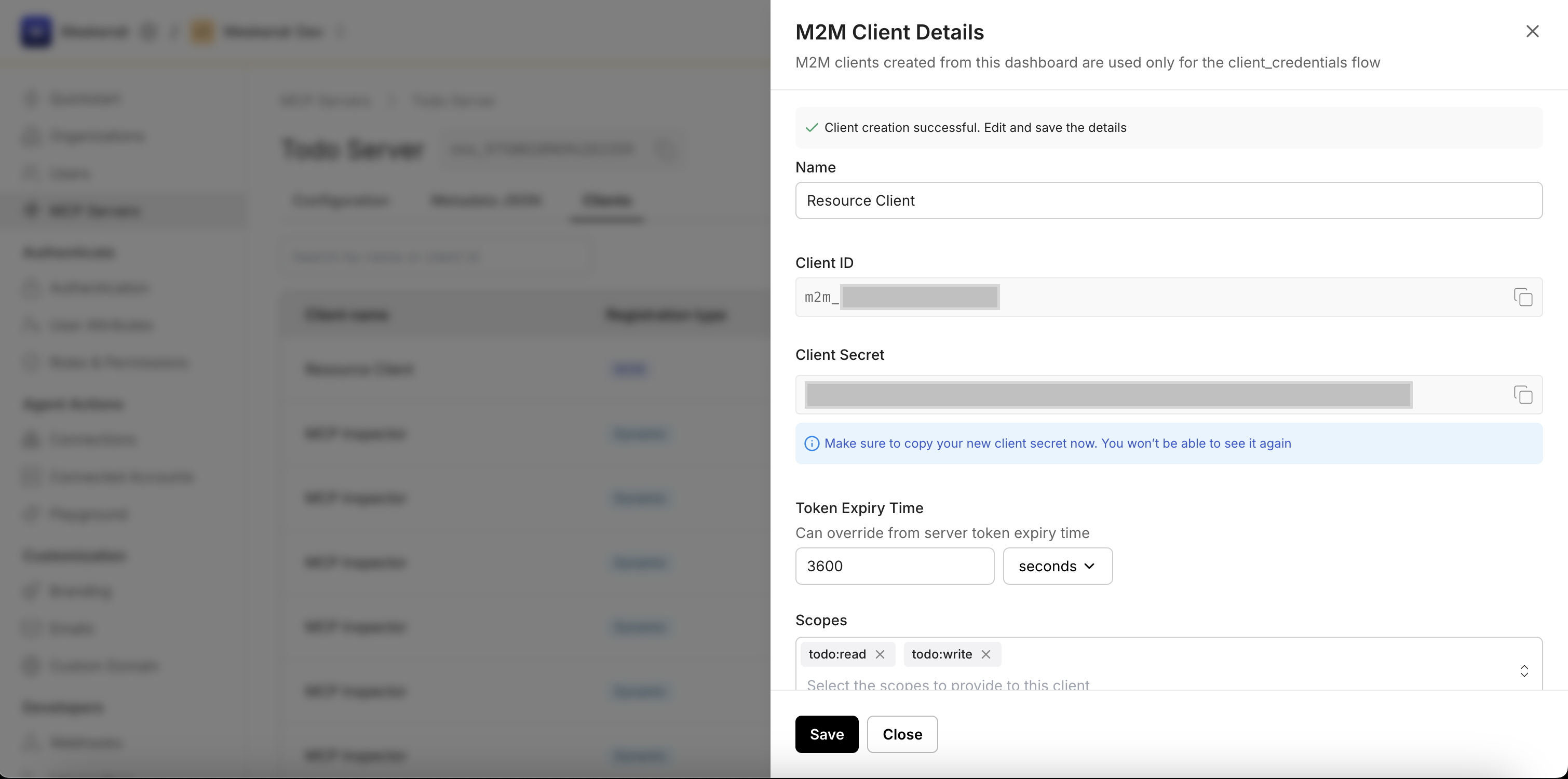
- Optionally, set scopes (e.g.,
todo:read,todo:write) that correspond to the permissions configured for your MCP Server. Hit Save
Requesting an Access Token
Section titled “Requesting an Access Token”Once you have the client credentials, the agent can request a token directly from the Scalekit Authorization Server:
curl --location '{{env_url}}/oauth/token' \--header 'Content-Type: application/x-www-form-urlencoded' \--data-urlencode 'grant_type=client_credentials' \--data-urlencode 'client_id={{client_id}}' \--data-urlencode 'client_secret={{secret_value}}' \--data-urlencode 'scope=todo:read todo:write'Scalekit responds with a JSON payload similar to:
{ "access_token": "eyJhbGciOiJSUzI1NiIsInR5cCIgOiAiSldUIn0...", "token_type": "Bearer", "expires_in": 3600, "scope": "todo:read todo:write"}Use the access_token in the Authorization header when calling your MCP Server’s endpoint.
Try It Yourself
Section titled “Try It Yourself”If you’d like to simulate this flow, use the same FastMCP Todo Server from the FastMCP Example.
Create an M2M client in the Scalekit Dashboard and run your token request using curl or programmatically within your agent. Once the token is obtained, attach it as a Bearer token in the Authorization header when calling your MCP Server’s tools.